sBridge Architecture Overview
The architecture includes three core layers: source chain (initiating chain), off-chain guardian network (validation layer), and destination chain (execution layer). A user initiates a bridge operation—either asset transfer or cross-chain execution—on chain1 by interacting with the Bridge Program, which generates a deterministic PDA as a cryptographic proof of intent. This transaction is indexed by multiple RPC providers and consumed by a decentralized guardian network.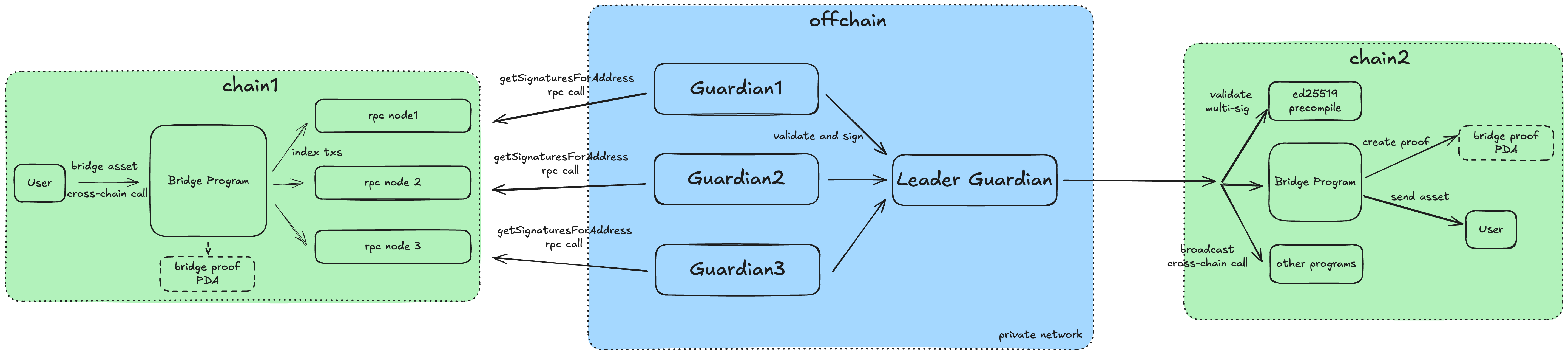
Core Layers:
- On-chain Program Layer: Handles transaction initiation, asset locking, and bridge proof (PDA) generation.
- Off-chain Guardian Network: Decentralized validators independently verify transactions, aggregate signatures, and forward proofs.
- Destination Chain Execution: Verifies proofs, executes transactions, and manages asset unlocking or minting.

